Security
Everyone plays a role in keeping our computing environment safe and secure. More than ever, both students and employees need to be vigilant to ensure that personal and campus computer equipment is safe and secure from the threats and risks that exist on today's networks and the world-wide-web. The best defense against malicious threats is educating yourself to recognize and deal with suspicious situations in the classroom, office, home, and on mobile devices.
In order to assist all CCAC users in acquiring the knowledge and skills to protect the college's information and technology assets, as well as to protect your own personal technology resources and privacy, the ITS Department has created an Online Safety and PC Security course, available in the Quick Links below. This online course includes videos produced by our ITS staff and relates practical knowledge and tips. There are also links to relevant resources and assessments to track your learning.
Security Tips
Cybercrime touches every facet of today’s society. It is the responsibility of every technology user to protect data. Many users do not realize that their everyday actions put not only their own information but also their families and their employers’ data at risk.
Mobile devices are becoming ever more popular, and cyber-criminals are well aware of it. It’s important that you guard your device, both physically and in terms of data protection. Probably the most popular method of gaining unauthorized access to email, and potentially other accounts, is what’s known as phishing when a would-be thief masquerades as someone you know or someone you should trust. Often they’ll try to bypass your healthy skepticism by creating fictitious scenarios where some threat exists, either to you or to your assets, or where there is supposedly a potential for significant gain.
File Sharing
The increase of people working at home has grown due to the current climate. This has caused the popularity and frequency of file sharing to increase.
So what is file sharing?
File sharing is making data available across a network for informational or calibration purposes. There is a variety of different methods of file sharing.
Never share copyrighted materials. For more information on college’s guidelines, view the Administrative Regulations Manual, section Copyrights and Fair Use Guidelines. Make sure you are following proper HEOA guidelines and FERPA guidelines.
*Sensitive Information can be classified in three distinct categories:
- Personal Identifiable Information (PII) is any representation of information that permits the identity of an individual to whom the information applies to be reasonably inferred by either direct or indirect means.
- Business information includes anything that poses a risk to the company in question if discovered by a competitor or the public. Such information can include trade secrets, acquisition plans, financial data, supplier, and customer information, among other possibilities.
- Classified Information pertains to a government body and is restricted by levels of sensitivity.
Recommended Method of Internal Sharing
SharePoint Team Site
A SharePoint Team Site is a web-based, members-only, site that allows a department, team, or functional area to store, organize, share, access, and collaborate on content.
SharePoint Team Sites are integrated with Microsoft Office which allows areas to collaborate on documents and other files with team members. SharePoint Team Sites can be used to store, organize and share Word documents, Excel workbooks, PowerPoint slides, and other file types.
Visit the help center article “Requesting a SharePoint Team Site”
Sharing a file through Email
Email can also function as a file transfer system. Every time you attach a document to an outgoing message, you are initiating a transfer of that data over the open internet.
Before sending data outside the college, ensure that you have reviewed the guidelines.
There are security risks involved in whichever method you select. Any time a person uses technology to share files between devices, File sharing can introduce risks of malware infection, hacking, loss or exposure of sensitive information. Without knowledge and security measures in place, the benefits of file sharing can be significantly outweighed by the potential for exposing the college’s sensitive data to new security threats.
Best Practices
- Plan your file structure
- Keep it simple
- Create an Effective Naming Convention
- Use terms that are easily recognized within your group
- Be Consistent
- Both in naming and structure –No exceptions, or changes midway
- Collaborating Effectively
- Limit Access- not everyone needs to see everything
- Establish Document Retention Levels
- Classify Security Levels
- Synchronization
- Set Automatic synchronization
- Create Regular Backups
- Security
- Create Strong Passwords
- Never Re-Use
- Use Encryption when transferring Sensitive Information*
- Keep your Software up to date with security Patches
- Install and maintain Anti-Malware/Virus protection software
Phishing Types
Phishing, Whaling, Spear-Phishing & Vishing
The highest number of cyber-attacks begin with email and social engineering. They are used to gain access to confidential data. People are extremely unguarded on social media and all the information that one puts out on the Internet is valuable to a hacker.
Phishing targets users through email, telephone, or text message. The Hacker poses as a legitimate institution to lure users into providing sensitive data such as personally identifiable information, banking, and credit card details, and passwords. The email may also come from a stranger promising monetary gain.
Spear-Phishing generally targets a specific individual. The individual usually has access to financial or account information in their line of work. The spear-phishing attacks are specifically geared to that individual and contain information that the user would find familiar.
Whaling targets specific companies. The hacker masquerades as an executive at an organization and directly targets individuals at the organization with the aim of stealing money or sensitive information or gaining access to their computer systems.
Vishing stands for voice phishing since it’s done over phone calls. The attackers are scammers making phone calls pretending to be someone else–often a legitimate business–to steal private information or money.
What should you know to avoid being a target?
- Be cautious of emails that come from unrecognized senders – senders you do not personally know – especially if they contain requests that are out of the ordinary.
- Reference the syntax used in the email.
- CCAC will never email you a link to request a mailbox increase, or other similar types of request.
- Only communicate personal information by phone or secure web sites. Look for sites that have the lock icon on the browser's status bar or an "https" URL. The s stands for secure.
- Do not click on links, download files, or open attachments in emails from unknown senders.
- Do not click on links, download files, or open attachments in emails from users that you know but it seems out of character, or not within their job scope.
- Never email personal or financial information.
- Beware of links asking for personal information. CCAC will never ask you to provide your password or any other personal information via email.
- When in doubt, do not risk it; do not open the email or click on the URL if you feel that the email appears strange. Report it.
- When using your CCAC account, click your Phish Alert Button.
- Beware of short messages from supervisors.
- Do not buy gift cards, or do wire transfers when requested for a payment.
- Permanently delete any suspicious emails that you receive in a personal email.
- Be wary of phone numbers, whether or not they seem familiar.
- Do not give out sensitive information via phone, unless you initiated the call.
- Put your name on the National Do Not Call Registry.
To find out more tips please visit the sites below:
If you suspect have been a victim, file a complaint with the FTC online or at 877-382-4357.
If it’s an online fraud, also report it to the FBI’s Internet Crime Complaint Center (IC3).
Ransomware vs. Scareware
Ransomware and Scareware are both forms malicious of software. While one is more serious than the other, both can infect your computer with irreversible damage.
Ransomware is more invasive than your typical malware. This infection locks the user out of files or their device and the only way to gain access is to pay the ransom. This malicious malware has cost companies millions of dollars. Even if the ransom is paid, it does not always guarantee that the files or device will be returned in the same condition it was in before the attack. It also does not guarantee that the hacker has not left software on the device to re-infect it at a later date.
What to Do:
- Back up your data on regularly basis
- Restore your computer
- Secure your login
- Ensure that you are using Antivirus software
If this is a college-owned computer call the ITS Service Desk at 412-237-8700 immediately.
Example of Crypto Locker
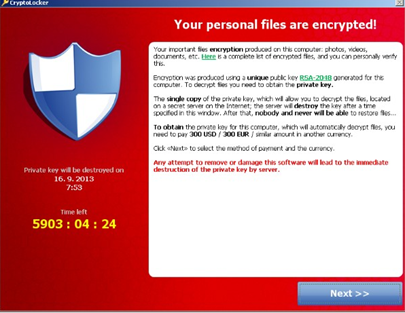
Scareware is malware that frightens a user into either purchasing software to “clean” their computer or actually infect the computer with malware. Scareware generally follows a typical pattern. Pop-ups will appear either as small warnings or appear as a whole web page.

What to Do:
- Check installed software, remove any with the date of the scareware pop
- Use Task Master to end the program
- Clear your cache and cookies in your browser
- Secure your login
- Ensure that you are using Antivirus software
If this is a college-owned computer call the ServiceDesk at 412-237-8700 immediately.
Best practices for safe computing:
- Be cautious of the websites you are accessing. Do not click on any advertisements or pop-ups on the web page.
- Many security updates and patches are pushed to all CCAC computers. When you receive a pop-up alerting you that a restart is necessary, make sure you proceed with restarting your machine as soon as possible so you receive the most recent security updates and patches.
- If you receive a suspicious email attachment, delete the email by selecting it and pressing shift + delete on your keyboard. This will bypass sending the email to the recycle bin and instead delete it permanently. Remember to never respond to spam emails and never click on any links within suspicious emails.
- Back up your data often using external media. Once the backup is complete, remove the media from your computer. If you leave the media connected, it may become infected and defeat the purpose of the backup. Perform a backup every few weeks.